Over the past few months, a new kind of spam email scam has joined the ranks of perennial favorites like the “Nigerian Prince who needs your help to move a huge sum of money” scam: the “FINAL WARNING” sextortion email.
There are many different versions of this scam, but one of the things they have in common is the use of personal information in the email. Most often they will use a password that you recognize but they may also use your phone number or name.
Did you get this email? You can relax – even if you do have a webcam, or visit the kinds of sites listed in the email – it can be safely deleted and should be ignored.
If they really have your password, they must have hacked you. Right?
This is an easy one to explain. There have been so many data breaches over the past several years that massive lists of emails and passwords exist online. (All the more reason to change your passwords frequently!) The scammers simply used one of those email lists, inserted your password in the email sent to your address, and waited for someone to take the bait.
This email in particular was very well crafted, because it took advantage of several triggers to induce panic:
- It uses a password you have used in the past (or still use!), making you think they have the ability to access things you thought were protected. (I really hope you change your passwords!)
- They use shame – particularly effective if you have ever visited any of the kinds of sites mentioned in the email. That song from Avenue Q wouldn’t be so funny if it wasn’t at least partly true!
- It references a well-known webcam hack news story. There was a popular case in 2013 involving a hacker taking control of the webcam of a Miss Teen USA and other women and using those photos for extortion. The case was well publicized enough that there is a good chance you probably heard of it, and know it is possible for someone to do this.
All the scammers want to do is to convince just a few people their threat is genuine – and get paid. It doesn’t take too many of those to make the scam profitable.
The Threat of Social Engineering
Very little ‘hacking’ involves using crazy technical wizardry to break into your computer – in fact, most of it just involves tricking you. Social Engineering is a term that describes a wide array of methods to get you to open the door for the hacker. Anytime someone deploys guile or subterfuge to trick you into granting them access they wouldn’t ordinarily have – that is Social Engineering. And Social Engineering is the way most people get scammed or have their device infected with malware.
It isn’t a new concept – and it has been used for longer than computers have been around. Remember the scene in Ferris Bueller’s Day Off, when Ferris has Cameron call the principal to get his girlfriend out of school? And to help convince Mr. Rooney that it really was her father, Ferris called on the other line? That’s Social Engineering.
You probably see Social Engineering attempts all the time. Have you ever encountered any of these examples?
- An email from “your bank,” warning you that your account has been compromised, and asking you to log in and verify your information?
- A pop up from a website (and not your antivirus!) warning you that your computer is infected?
- A text from an unfamiliar number, letting you know that you won a prize?
- A phone call from ‘Microsoft,’ telling you that they’ve detected malware on your system?
Some text from “Final Warning“:
I’ve been watching you for a while because I hacked you through a trojan virus in an ad on a porn website. If you are not familiar with this, I will explain this. A trojan virus gives you full access and control over a computer, or any other device. This means that I can see everything on your screen and switch on your camera and microphone without you being aware of it.
The Final Warning email scam scared a lot of people. If you think about it – if they really did break into your system and had the ability to do all of the things they claimed they could – don’t you think they would have included a screenshot?
How Can You Protect Yourself?
Safe browsing strategies and good passwords are both excellent ways to protect yourself. I’ll cover password selection in a future article, but a few tips for browsing:
- Update your antivirus! If you don’t have one, get one!
- Don’t click a link or open an attachment – instead, open your browser, manually browse to the website, log in, and find the message. Anything “official” sent to you by email should be accessible directly through your online account.
- Hover over links in your emails, and look at what URL they are actually sending you to. Don’t click links to shortened URLS like a bit.ly link if you don’t know exactly where it is going, and be mindful of fake URLs that include the real name somewhere in the link (like chasefraud.com instead of chase.com or facebook.scammersite.com instead of facebook.com). Do remember this applies to emails, and not to other documents – sometimes hovering in an Office document can launch a malicious script!
- If you decide to call instead of click, don’t call the number in the email! If the link is bad, the phone number might be suspect as well!
- Don’t take Facebook quizzes! You know the ones I mean – the ones that ask you all sorts of questions like the street you lived on, your favorite pet, or what your first concert was? You notice how similar those lists of questions are to security questions you fill out when you open an account?
- Don’t try to get something for free that you would ordinarily have to pay for! Ethics of piracy aside, offering premium content for free is frequently bait used to lure unsuspecting browsers.
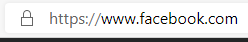 Look for a secure connection! In the address bar of your browser, you will either see ‘http://’ or ‘https:/’ before the site address. The ‘s’ is very important. Along with the lock symbol (which varies between browsers), that indicates you are connecting to a website with a secure connection. If you are going to enter in any information, from a password to a credit card number, make sure that ‘s’ is there!
Look for a secure connection! In the address bar of your browser, you will either see ‘http://’ or ‘https:/’ before the site address. The ‘s’ is very important. Along with the lock symbol (which varies between browsers), that indicates you are connecting to a website with a secure connection. If you are going to enter in any information, from a password to a credit card number, make sure that ‘s’ is there!- Don’t use free public wifi. Really, it isn’t a good idea. You wouldn’t yell out your credit card number inside of a coffee shop, would you? When you send out any kind of data on a Public Wifi, it is easily picked up and stolen. Not a good idea at all.
ReadeTech is available if you would like to have a safe browsing training session, or if you just want to talk about your current safe browsing strategies to see if there is something you may have missed. (Contact us today!) If you just want a simple rule of thumb – just remember to always be suspicious. And if you aren’t sure, don’t click on it! Sometimes it is better to take an extra couple of minutes to verify over the phone rather than lose time and money falling for a phishing scam!